Blog
Cybersecurity Risk Assessment: Create Your First One Now
Almost every organization on the earth sends data across the Web, posing a possible risk of cyber attack. There are several emerging cyber security issues that it’s essential to look out for in the approaching years. These attacks are targeting health departments, education sectors, and businesses.
Cyber attacks are common and may result in data corruption, hijacking of files, and even data breach. Nonetheless, it might be much worse in the event you lost the info perpetually, akin to the hacker’s attack on the Zoom application where greater than 500,000 Zoom passwords were stolen.
All of those passwords and credentials were available on the market or were distributed on dark web platforms. Several accounts that belonged to varied businesses and individuals were greatly affected.
What’s a Cybersecurity Risk Assessment?
A cybersecurity risk assessment is the technique of researching, identifying, and highlighting information security risks which are present in your system. Risk assessments analyze and discover the possibilities of risk from attacks akin to:
- Phishing.
- Malicious spyware.
- Cross-site scripting (XSS).
- Credential stuffing.
- Denial of Service (DoS).
- SQL injection.
- Session hijacking and man-in-the-middle.
Why is a Cybersecurity Risk Assessment Essential?
A cybersecurity risk assessment is sort of necessary to discover security vulnerabilities in your system. A comprehensive cybersecurity risk assessment will provide a framework to determine and update a corporation’s information security policies and guidelines. These assessments play a major role in securing the interior and external information of any organization.
Eliminating the risks which are identified during risk assessment will avoid and reduce the possibilities of pricey breaches happening from common security issues. It is going to also assist in eluding any relevant compliance issues.
Through the technique of risk assessment, everyone will follow the cybersecurity rules which is able to eventually create a risk-aware and proactive cybersecurity culture within the organization.
What are the Advantages of Performing a Cybersecurity Risk Assessment?
There are several advantages of performing risk assessments that can assist in strengthening the safety barriers of any organization. Listed below are the highest five:
1. Improvement of Organizational Security Knowledge
Cybersecurity risk assessments will discover all organizational vulnerabilities. It is going to also offer you a transparent idea concerning the places where your organization needs to enhance.
2. Reduction of Expenses
After identifying and analyzing vulnerabilities, you may create a talented team that can eliminate these vulnerabilities. As well as, the danger assessment will reduce the time, effort, and possibilities of experiencing malware incidents that will cause data corruption or revenue loss.
3. Template for Future Assessments
As cybersecurity risk assessments are needed constantly, it’s best to consider investing your money and time in creating risk assessment guidelines that could be followed for future uses.
4. Avoidance of Security Incidents
Cloud security incidents cause a considerable reputational impact on any organization. The chance assessments will save your organization’s popularity by avoiding the incidents altogether.
5. Protection Against Data Loss
Cybersecurity risk assessments are the important thing to protecting your confidential data. Any stolen vulnerable data will cause a burden to your organization, and 60 percent of companies that have breaches are out of business inside 6 months. Sensitive data includes:
- Mental property.
- Strategic plans.
- Marketing campaigns.
- Internal operations documents.
- Trade secrets.
Hence, cyber risk assessments are fundamental in carrying out information risk management.
5 Steps to Create Your First Cybersecurity Risk Assessment
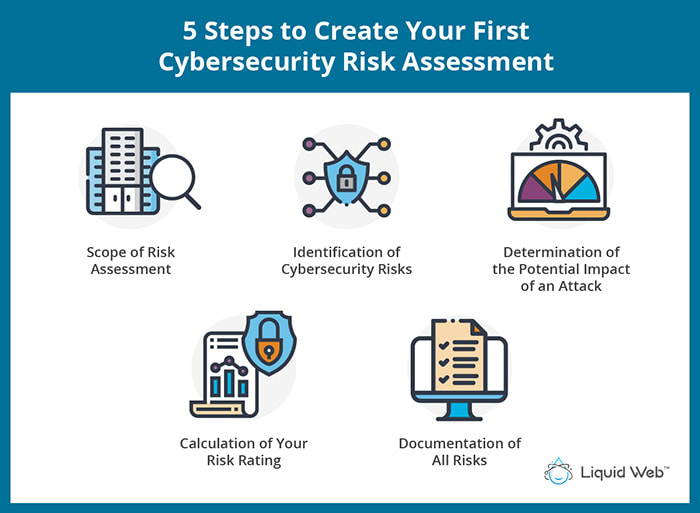
A cybersecurity risk assessment must include scoping, risk identification, risk evaluation, risk evaluation, and documentation.
1. Scope of Risk Assessment
Determine what’s included within the scope of the danger evaluation. The scope can consist of a specific department, unit, or the whole organization. Nonetheless, an organization-wide risk assessment is sort of complex and difficult to do. You will need to have the support of stakeholders across all departments, as you would need to take their input while categorizing the scope.
2. Identification of Cybersecurity Risks
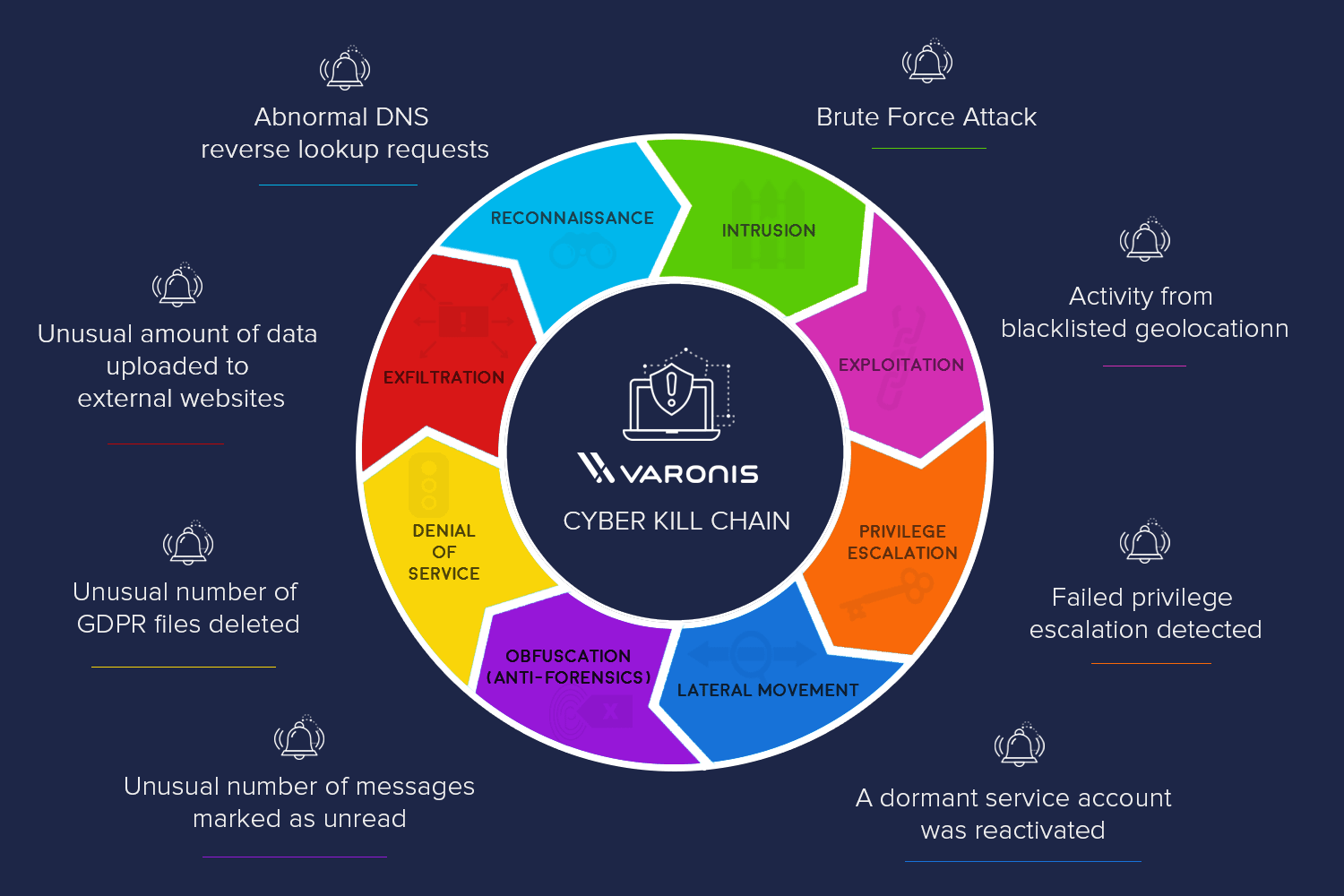
Discover a listing of physical and logical assets to be included in the danger assessment scope. Then, analyze the first threats to the listed assets. For the identification of potential threats, a cyber-kill chain map can offer you a superb view of the stages of an actual attack. Summarize all potential threats in easy words to make them comprehensible for the stakeholders.
3. Determination of the Potential Impact of an Attack
The term risk likelihood means the probability of the exploitation that a given threat could cause based on the discoverability of vulnerabilities in the current system. You may create specific keywords to know the degree of the potential impact of a cyber attack.
Organizations can select to categorise potential impact using the next keywords:
- High Impact implies that the impact could possibly be immense.
- Medium Impact implies that the damage done could be recovered with some effort.
- Low Impact implies that the impact can be minimal.
4. Calculation of Your Risk Rating
Next, calculate the danger rating utilizing keywords just like the potential impact in step three:
Risk Rating = Potential Impact x Risk Likelihood
Listed below are examples of how organizations can rate their risk and threat levels:
- Severe implies that the threat is critical and risk should be eliminated immediately.
- Elevated implies that a possible threat exists throughout the organization, which should be eliminated in a given period.
- Low implies that the threats are typical and it’s best to eliminate them, but these threats can only cause a small impact on the organization.
5. Documentation of All Risks
The last step is the documentation of all risks in a risk register. The document must be reviewed usually, and each latest risk or risk scenario should be written on this document. The documentation of such risks will make it easier for the organization to know cybersecurity risks.
The chance documentation must include:
- Consequences of risks.
- Identification date of risks.
- Current security measures.
- Present-day risk level.
- Motion plan.
- The progress status of the motion plan.
- Residual risk: The extent of risk after the motion plan is executed.
- Risk owner: Who’s accountable for ensuring that each one the risks are eliminated.
Governance and Compliance Considerations
Nonetheless, it’s important that organizations ‘retain documented information concerning the information security risk assessment process’ in order that they’ll validate that they comply with all the stated requirements in the rule of thumb.”
Organizations must follow these steps and create relevant documentation as a component of the data security risk treatment process.
Clause 6.1.2 of the usual guideline sets out the standards of the data security risk assessment process. Organizations must:
- Be sure that certain information security risk guidelines must be established and maintained.
- Confirm that repeated risk assessments will produce consistent, valid, and comparable results.
- Discover risks related to lack of confidentiality and integrity, and discover the individuals accountable for those risks.
- Analyze and evaluate security risks in line with the usual guidelines.
Fully Managed Hosting Can Do This For You
Cybersecurity is a fancy process that requires considerable planning and knowledge. Let Liquid Web be your cybersecurity partner as your online business grows into the longer term.


