Blog
Understanding the Importance of Cloud Security
Cloud computing has change into a necessary a part of the fashionable business landscape. It offers a variety of benefits, including scalability, flexibility, and cost-efficiency. Nevertheless, as organizations move their data and applications to the cloud, data breaches and cyber threats have change into increasingly prevalent.
That’s why understanding and implementing effective cloud security measures is not any longer optional – it’s crucial!
Cloud security is a posh topic, nevertheless it is important to know the risks related to cloud computing and take the mandatory precautions. With this in mind, this exhaustive guide will uncover the prominence of cloud security, delve into its challenges, and explore the differing types of cloud environments and their security implications.
Whether you are an IT skilled, a business decision-maker, or just fascinated by cloud security, this guide goals to equip you with the knowledge and resources it’s essential secure your cloud environment effectively!
Understanding the importance of cloud security
Imagine an enormous virtual space where you may store your files, access applications, and even power complex processes without the constraints of your local device – that is cloud computing.
At its heart, cloud computing delivers various services over the Web, from storing data to running apps. It is a paradigm shift empowering individuals and businesses alike to transcend the constraints of traditional computing, offering unparalleled convenience and efficiency.
Nevertheless, as our reliance on the cloud grows, so does the importance of safeguarding sensitive data and demanding systems from potential cyber threats. A staggering 80% of US firms report that their systems have been compromised. This underscores the urgent need for robust cybersecurity measures.
Cloud security involves a series of measures designed to guard data, applications, and infrastructure inside the cloud environment. It offers a large number of advantages that reach beyond just protection against external threats, including:
- Data loss prevention — Data loss can have devastating consequences, each financially and reputationally. Robust cloud security measures help prevent unauthorized access to sensitive information and mitigate the danger of knowledge loss, whether from malicious attacks or easy human error.
- Regulatory compliance — Cloud security aids in ensuring compliance with the stringent data protection regulations of varied industries and avoiding hefty penalties and legal issues.
- Business continuity — Implementing security measures, resembling data backups and disaster recovery plans, helps businesses make sure the continuity of their operations, even within the face of a disaster or system failure.
- Multi-tenancy security — Cloud environments often host multiple tenants. Robust security protocols are mandatory to stop data leakage between tenants and uphold individual privacy.
- Vulnerability management — Regular security assessments and updates are vital to discover and mitigate potential vulnerabilities inside the cloud infrastructure and applications.
As cyber threats evolve, cloud security becomes greater than just safeguarding a business’s data; it’s about ensuring operational continuity and maintaining customer trust.
Challenges and risks in cloud security
Unfortunately, navigating the realm of cloud security is not without its difficulties that demand meticulous attention.
Mitigating data breaches
Some of the significant concerns in cloud security is the potential for data breaches. As organizations entrust their sensitive information to third-party cloud providers, the danger of unauthorized access becomes ever more pronounced.
High-profile breaches in recent times have accentuated the magnitude of this challenge, demonstrating that even major players within the industry are usually not impervious. The truth is, the sheer volume of knowledge stored within the cloud and the various entry points for potential attackers amplify the issue of safeguarding information and increase the attack surface. Furthermore, the common cost per data breach has been reported to be as high as $4.35 million.
Organizations must employ robust encryption methods and access controls to mitigate this risk. A proactive approach, coupled with regular data security assessments, is imperative to remain one step ahead of cybercriminals.
Understanding the role of shared responsibility
Cloud security operates under a shared responsibility model, wherein each the cloud provider and the user bear specific security responsibilities. This collaborative arrangement, while fostering efficiency, can even blur the lines of accountability.
Under this model, the cloud service provider is answerable for the safety of the cloud. This includes securing the underlying infrastructure that supports cloud services, resembling hardware, software, networks, and facilities.
However, the user is answerable for security within the cloud. This involves protecting the info stored within the cloud, managing access to this data, securing applications, and implementing client-side data encryption.
Failing to know and fulfill these responsibilities can leave chinks within the armor of an otherwise well-protected system. Ambiguity in roles can result in:
- Security gaps and neglected vulnerabilities.
- Patch and update management negligence.
- Inadequate controls that risk unauthorized access.
- Data breaches resulting from misconfigured settings.
Navigating compliance and legal features
These regulations are designed to uphold privacy, prevent data breaches, and ensure data integrity, making them an important aspect of any cloud security strategy.
Non-compliance can have severe legal implications, resembling hefty fines, lawsuits, and significant reputational damage. As an example, under GDPR, firms might be fined as much as 4% of their annual global turnover or €20 million (whichever is higher) for serious infringements.
On the brilliant side, these challenges are usually not insurmountable. There are a number of solutions available to mitigate these risks, like using:
- Firewalls.
- Encryption methods.
- Multi-factor authentication and efficient access controls.
- Regular security audits.
- Penetration testing.
- Staff training.
It is also vital to remain updated with regulation changes and adjust security practices accordingly.
Nevertheless, since managing all these security features might be an intricate endeavor, particularly for businesses with out a dedicated IT security team, outsourcing to a trusted provider, like Liquid Web, might be helpful. Organizations must meticulously select cloud providers that supply transparent cloud data handling practices and robust security measures that align with regulatory requirements.
Several types of cloud environments and their security implications
The cloud environment that a business chooses can significantly impact its security considerations. This decision hinges on the understanding of 4 major cloud models: public, private, hybrid, and multi-cloud environments.
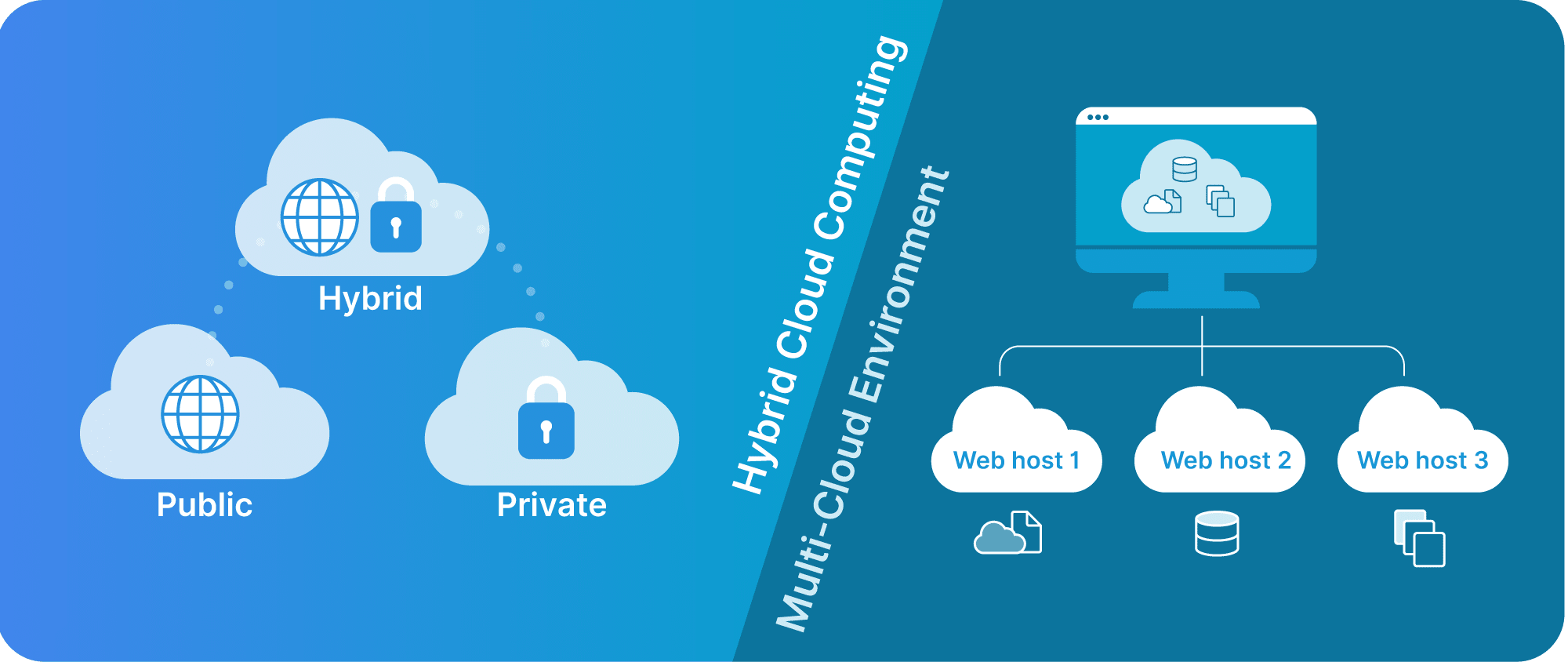
Public clouds
Public clouds are just like the bustling city squares of the digital realm. They’re shared platforms provided by third-party service providers, resembling Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). Their cost-effectiveness and straightforward scalability draw organizations of all sizes to public clouds.
Yet their openness poses security concerns. The multi-tenancy nature of public clouds means data from different clients is stored on shared resources, posing a risk of cross-access and potential data breaches.
Moreover, businesses largely depend on the cloud provider’s security protocols, which might vary in strength and comprehensiveness. Adequate measures, resembling encryption and robust access controls, change into crucial to keep up the integrity and confidentiality of sensitive information.
| Pros | Cons |
|---|---|
| Cost-effective and scalable. | Shared resources increase security risks. |
| Accessible from anywhere. | Limited control over infrastructure. |
| No maintenance burden. | Potential for vendor lock-in. |
| Big selection of services available. | Data sovereignty concerns. |
Private clouds
Private clouds are the exclusive gated communities of the cloud landscape. They’re dedicated environments utilized by a single organization, providing greater control over resources and data. That’s why industries with stringent compliance requirements, like finance and healthcare, often prefer private clouds.
While this setup provides more control over data and processes, it still requires vigilant monitoring and management to stop insider threats and ensure regulatory compliance. A talented in-house security team may be essential because the responsibility of securing the infrastructure lies with the organization. Also, the danger of outgrowing the private infrastructure might result in compromised security.
| Pros | Cons |
|---|---|
| Enhanced security and control. | Higher initial setup and maintenance costs. |
| Compliance with stringent regulations. | Limited scalability in comparison with public clouds. |
| Isolated environment for sensitive data. | Resource underutilization. |
| Reduced risk of shared vulnerabilities. | Internal expertise is required for management. |
Hybrid clouds
Hybrid clouds mix elements of each private and non-private clouds. This approach allows organizations to leverage the benefits of each environments, tailoring their setup to specific needs.
As an example, sensitive data might be stored within the private segment, while non-sensitive operations can reap the benefits of the general public segment’s scalability.
While this model offers flexibility, it also brings about its own set of security challenges. The complexity of integrating private and non-private environments can create security inconsistencies, and the movement of knowledge between these environments can expose it to vulnerabilities.
| Pros | Cons |
|---|---|
| Flexibility to balance private and non-private cloud models. | Complex architecture to administer. |
| Scalability combined with control. | Potential for security policy mismatches. |
| Reduced risk of vendor lock-in. | Integration challenges between the private and non-private clouds. |
| Cost optimization based on use cases. | Requires specialized expertise. |
Multi-cloud environments
The multi-cloud environment involves using services from multiple public cloud vendors or combining private and non-private clouds.
This strategy reduces dependency on a single provider, prevents vendor lock-in, and offers redundancy, nevertheless it also amplifies security challenges. Different providers have varied security protocols. Coordinating security protocols, compliance requirements, and data transfers between disparate clouds demands meticulous planning to make sure consistent protection.
| Pros | Cons |
|---|---|
| Hosting provider diversity prevents vendor lock-in. | Complex management across multiple vendors. |
| Enhanced redundancy and resilience. | Integration and compatibility challenges. |
| Optimized pricing and repair selection. | Increased risk of inconsistent security. |
| Tailored solutions for specific needs. | Potential for increased management costs. |
Ultimately, deciding which cloud model to employ will depend on the organization’s goals and requirements.
Whatever the chosen cloud environment, Liquid Web can assist businesses of their journey toward full-bodied cloud security. Liquid Web’s customizable dedicated infrastructure offers a viable solution, especially for giant enterprises with unique hosting needs.
Constructing a sturdy cloud security strategy with Liquid Web
Constructing a sturdy cloud security strategy is a multifaceted task that involves several key elements. Implementing strong access controls, recurrently patching and updating systems, encrypting data, and monitoring for suspicious activity are all binding steps in making a secure cloud environment.
Cloud security tools and solutions play a big role in implementing this strategy. They supply proactive protection, detect threats, and respond routinely to potential attacks, ensuring data privacy, integrity, and availability within the cloud.
That is where Liquid Web, a pacesetter in managed hosting and cloud services, steps in to supply comprehensive cloud security solutions that mix cutting-edge technology with expert guidance. This includes:
- Advanced threat detection — Liquid Web employs cutting-edge threat detection tools to watch cloud environments repeatedly and take swift motion to neutralize threats.
- Multi-layered defense — A robust security setup requires multiple layers of defense. Liquid Web implements firewalls, intrusion detection systems, and encryption mechanisms to make sure your data stays inaccessible to unauthorized entities.
- Regular security audits — Security is an ongoing process. By conducting regular security audits and vulnerability assessments, Liquid Web can discover weak points in your infrastructure and stop breaches before they occur.
- Disaster recovery planning — Liquid Web helps you develop a comprehensive disaster recovery plan, ensuring business continuity even within the face of adversity.
- 24/7/365 support— Cyber threats don’t adhere to a schedule. Liquid Web’s experts work across the clock, monitoring and responding to security incidents in real time.
One example of a business that has successfully implemented a tenacious cloud security strategy with Liquid Web is Crazy Engineers. Kaustubh Katdare, the founding father of Crazy Engineers, praised Liquid Web’s tailored solutions and exceptional support.
Crazy Engineers’ global community faced significant uptime and security challenges, including a significant hack. Liquid Web stepped in to supply reliable hosting, boosting the location’s resilience to handle a 70% traffic increase and enhancing database speeds by 330%.
It’s clear that Liquid Web’s secure, fast, and reliable hosting can play an important role in helping businesses execute their cloud security strategies effectively. With a 99.999% uptime guarantee and fast loading times, Liquid Web ensures a smooth online experience for purchasers while providing the hardy security businesses need.
With Liquid Web, businesses can confidently tackle the complexities of cloud security, knowing they’ve a trusted partner by their side.
Take the subsequent step in cloud security with Liquid Web
Navigating the complexities of cloud security can seem overwhelming, nevertheless it’s a necessary task in today’s digital landscape. From understanding the differing types of cloud environments and their security implications to managing the shared responsibility model and legal compliance, businesses must take a proactive approach to guard their data, applications, and infrastructure.
Constructing a sturdy cloud security strategy is a critical step on this journey. Implementing strong access controls, recurrently updating systems, encrypting data, and monitoring for suspicious activity can significantly enhance a business’s security posture. Cloud security tools and solutions, like those offered by Liquid Web, are mandatory.
Liquid Web’s services are designed to cater to the unique needs of companies, offering solutions like fully managed hosting, private cloud hosting, high availability hosting, compliant solutions, and customizable dedicated infrastructure. With 24/7 human support and hassle-free migrations, Liquid Web provides businesses with the reassurance they should concentrate on their core operations, knowing their cloud security is in secure hands.

