Blog
Host-Based Intrusion Detection System: A Guide
Security threats could cause serious harm to online businesses. Attackers use various tools and techniques to do malicious activities inside the network, all of those impacting the corporate’s revenue. Hence, it is crucial to have tight security to your network systems. Any intrusion may end up in severe financial and reputational loss. A number of the common security issues include policy breaches, unauthorized network penetration, or insider attacks. That is where an intrusion detection system (IDS) might help. It analyzes activity and sends an alert notification if any suspicious activity is identified.
This guide incorporates all of the relevant information you could understand the mechanism of a host-based intrusion detection system and the way it really works.
What’s a Host-Based Intrusion Detection System (Host-Based IDS)?
A number-based intrusion detection system (HIDS or host-based IDS) uses integrated intrusion signatures to detect potentially-suspicious activities that would cause damage to your network system. It helps you retain your devices constantly in check by observing applications and devices running in your system with a view to prevent an intrusion. Host-based IDS provides software that tracks changes and processes the data collected from computer systems.
What Does a Host-Based Intrusion Detection System IDS Do?
Listed below are five things you possibly can expect a HIDS to perform:
- Evaluate Traffic: Evaluate the incoming and outgoing traffic on a selected computer on which the IDS software is installed.
- Signature-Based Detection: Utilize a signature-based detection method to match the signatures present in the network traffic against a database of malicious signatures.
- Threat Intelligence: Accommodates threat intelligence features reminiscent of HIDS agents which help recognize and eliminate any malicious activity present inside the system.
- Monitor Critical Files: Scrutinize critical system files.
- Notification of Intrusion: Discover and notify you if there was any try to overwrite critical files.
Hence, your devices and applications will remain protected all the time.
How Does a Host-Based Intrusion Detection System Work?
Here is how a host-based IDS works:
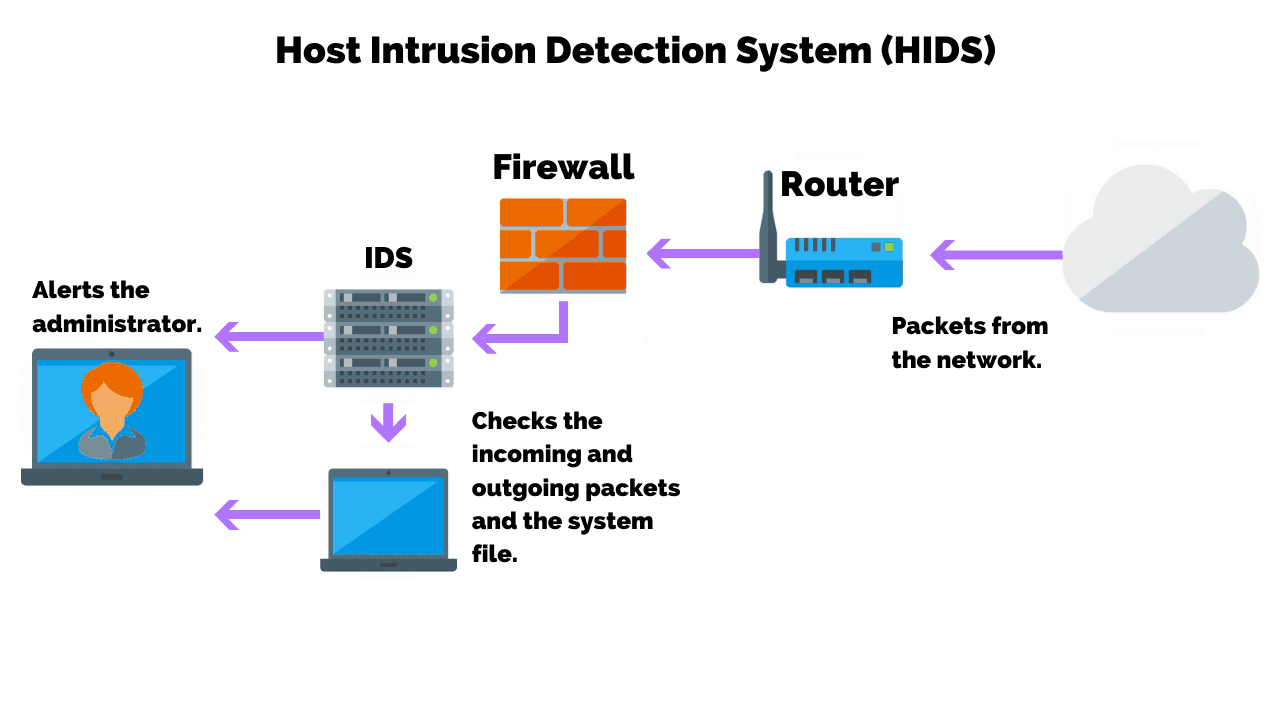
- Data Collection: The IDS collects the information from computer systems.
- Network Statement: The IDS observes the network traffic and matches all of the traffic patterns to all known attacks. This method can also be referred to as pattern correlation.
- Activity Detection: The IDS confirms if a very unusual activity was a cyber attack or not.
- Activity Alert: Once suspicious activity is confirmed, the IDS will warn you via an alarm. These alarms will allow you to quickly find the reason for the problem so your team can stop the attack.
What Systems Does a Host-Based Intrusion Detection System Protect?
The host-based IDS system detects threats and patterns of attack inside your network system. It protects all of your worthwhile data assets. With the rise of security trends, HIDS helps protect the cloud environment on which it’s installed. It could actually work on different platforms reminiscent of AWS, Microsoft Azure, or Liquid Web. There are different IDS systems for Windows, Linux, and Mac.
What Threats Does a Host-Based Intrusion Detection System Shield Against?
There are numerous threats that could be eliminated with the assistance of a host-based IDS:
1. Malicious Attacks
At any time when malicious activities occur inside a system reminiscent of unauthorized authentication attacks, HIDS detects the attack and sends it for evaluation. Once a cyber attack is confirmed, it generates an alert and can send the data in regards to the attack to you. This real-time monitoring helps to attenuate the damage when an attack happens.
2. Asymmetric Routing
When data packets traveling through the network take a selected path to their destination and take a special route back, it known as asymmetric routing. This mechanism allows the attackers to perform a DDoS attack. HIDS helps determine such routes and can ask you to show these routes off for enhanced network protection.
3. Buffer Overflow Attacks
When more data is written than a buffer can handle, it known as a buffer overflow, and it might cause the whole system to collapse. This sort of attack attempts to infiltrate segments of memory within the device on which the host-based IDS is installed. It replaces the conventional data in those memory locations with suspicious data, which will likely be implemented later in an attack. In nearly all of cases, buffer overflow attacks are intended to show right into a type of DDoS attack but may also be used to disclose sensitive information or perform distant code execution. A number-based intrusion detection system will help eliminate such attacks by identifying the patterns related to this attack type.
4. Scanning Attacks
Scanning attacks involve sending data to the network to gather data in regards to the network, traffic, ports, and hosts. Attackers often attempt to discover open ports where a virus could be inserted to make an attack within the system. Nevertheless, a host-based intrusion detection system prevents the attacker from stepping into the system in the primary place. Within the event that an attacker is in a position to breach this initial level of protection, a HIDS will help minimize these attacks using advanced features reminiscent of a web application firewall to guard the information inside the system.
Use Cases for Host-Based Intrusion Detection System

Listed below are two use cases that exemplify how IDS is evolving businesses throughout the world:
Supply Chain Management
As an intrusion detection system provides tracking and tracing systems, you possibly can easily mix them with digital services to make the supply chain more successful. Materials could be identified with the assistance of barcodes or RFID technology. With using such a system, trusted shareholders inside an organization can get information via the IDS data framework, which can make the availability chain industry safer and cloud monitoring easier.
HIPAA and PCI Compliance
Your organization can have some standard requirements which you have got to fulfill with a view to work. With an IDS, your organization can easily meet requirements reminiscent of HIPAA compliance and PCI compliance.
Why Select Threat Stack Host-Based IDS and Liquid Web
Liquid Web’s Threat Stack host-based IDS delivers substantial security advantages to clients for a small price. It also provides full-stack cloud security with uninterrupted protection in monitoring, reporting of any identified security threats, and delivery of IDS inside the system’s network to make sure the security of the devices from attackers.
Threat Stack helps provide more comprehensive security to your systems and pairs with Liquid Web’s 24/7/365 support. Contact us now to learn more about Threat Stack.


